Of course, the most important news last week was the publication of “Collection #1” — a database consisting of 2.7 billion pairs of "email: password", and 773 million unique records. The leak was already covered in detail in the previous post. Now let's talk about what you should do to protect yourself.
Passwords have long been recognized as an unreliable means of protecting accounts on the network. With a high probability, all your ten-year-old passwords are already available to attackers due to the mass of large and small leaks from Linkedin, Twitter, Tumblr, MySpace and Yahoo. Spoiler: There is no simple solution to the problem, but there is a set of actions that will help reduce the risk of hacking important accounts.
If you are subscribed to Troy Hunt's HaveIBeenPwned service, last week you were 34% likely to receive a similar message:
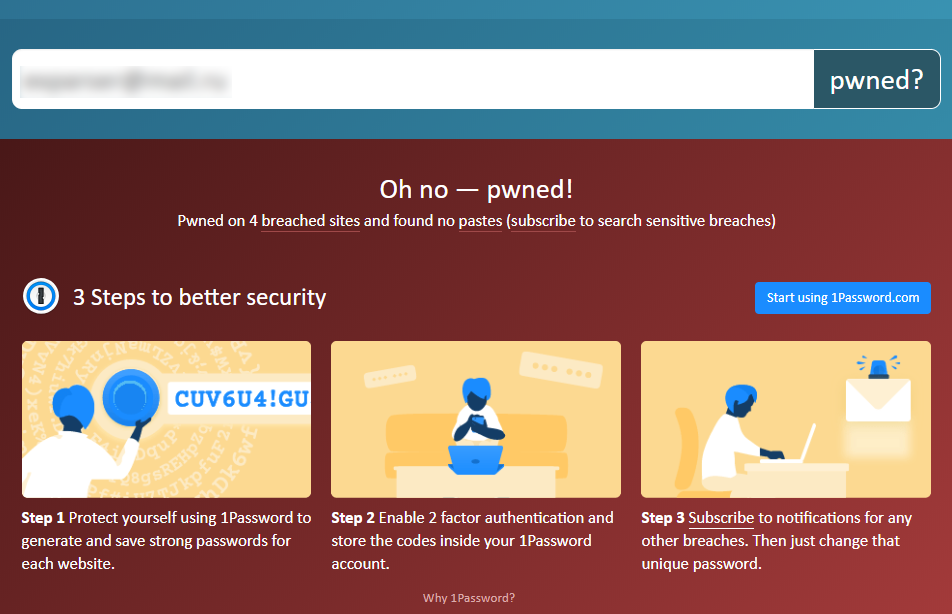
Ok, your email address is in the database, what's next? You can go to the website and see where this address appeared previously, and check other addresses. In the case of long-used addresses, we found them in a dozen different hacker password bases. A logical question arises: which passwords have leaked? What services need to change the password? If the password database of a particular service was published. Then one could answer at least the second question. But “Collection #1” does not allow to answer any of the questions posed. This database of compromised passwords is simply a compilation from various sources of unknown origin.
Well, in the same service, you can check your own passwords. If you do not trust Troy Hunt, you can download a database of hashed passwords and check your passwords offline. But at least someone in this world must sometimes be trusted!
Who is to blame for the fact that your password was available to attackers? There may be many answers. The obvious one is the leak of the password database of some kind of network service. In the Collection #1 dump, there are a huge number of small sites and forums that have been hacked at various times. About once every couple of years, data leaks from large services occur. But the problem is not only data leakage.
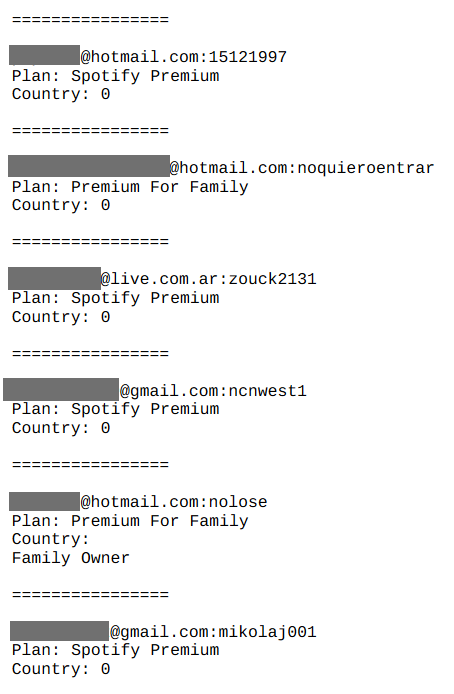
The screenshot is taken from this Troy Hunt post in response to suspicions of stealing the password database from the Spotify music service. The service was not to blame: using the login-password pairs already known from other leaks, the attackers were able to crack many Spotify accounts, including accounts with a paid subscription. This is a clear consequence of reusing the same password. But that's not all. Your passwords are stored in the browser, you enter them on different computers and mobile devices. This data can be stolen also on your side. Finally, many sites not only have poor protection against theft of personal information of users — they do not even use HTTPS, which means that your password to such a service is sent in clear text and can be intercepted. You could also become a victim of phishing and not even notice it (“well, I could not log in, then try again”).
All this creates a rather unpleasant situation for the average user when there is no clear understanding of what happened and what the consequences will be. Leaking passwords from one service can result in cracking another using the same password. You (or, even worse, your technically untrained relatives) can be blackmailed, while using the real password of one of your accounts. An attacker can steal real money by hacking into payment services and websites storing your credit card information. Captain Evidence would recommend some password manager to solve the main problem — password reuse. But in fact, not everything is so simple.
The story of the next major password leakage is a story about OPSEC, operational security (a term borrowed from the military). The meaning of OPSEC is that protecting your data is a continuous process. There is no one reliable method that solves all problems once and for all. Suppose you are using a password manager. Have you changed your password on all sites? What about long forgotten forums? Can an attacker use phishing to bypass the password manager or any other protection? Yes, he can.
Two-factor authentication adds another level of protection to your account. Is it possible to bypass it? It is. There are enough examples of successful bypassing authorization via SMS, using, for example, social engineering for the cloning of a SIM card. More recently, a proof-of-concept interception of data entered by the user during 2FA authentication has been shown. In December, an Android Trojan to steal funds from PayPal was appeared, which doesn’t steal passwords or 2FA tokens at all, but waits for a login to the legit application and takes control of it.
The right approach to data security involves using a combination of technical tools to protect accounts, such as a password manager and two-factor authentication, plus security-oriented software and devices use. This is not an exhaustive list of methods, we just give advice and give examples. Probably, you should not bind the accounts of working tools to a personal e-mail. It is definitely worth having a separate email for the vulnerable services— old, but useful forums without https and the like. Or vice versa, you can create an e-mail account for the most important services, not show it on the web, not conduct correspondence with it and protect it as much as possible with all available means. In the event of a leak, attackers will receive an email address for “insecure” services and will not be able to use it to attack your critical accounts. The main thing: do not get lost in your own opsec-rules.
Let's add here the refusal to install questionable applications on the smartphone and the desktop, or even better, install antivirus software, this also does not solve all the problems but makes a tangible contribution to the common security box. Carefully protect your smartphone from other people's access, as it usually contains the keys to all doors. Even these measures do not exclude the regular change of passwords on the most used services with a certain frequency. The frequency of this procedure depends on your personal degree of paranoia, but every six months should be more than enough. Make a list of important services, put a reminder, do not save billing data when you are offered this, even if it is eBay or Aliexpress.
Do all of these methods provide a 100% guarantee for the protection of your data? No, they don’t, it does not happen at all in the field of information security. But they will sufficiently protect you not only from the method of credential stuffing when hackers try to apply the leaked passwords from the list to any services but also from some other sophisticated methods. And in this case, if you receive a letter from HaveIBeenPwned, this will not be a reason for panic, but a trigger for performing the usual security verification procedure for your own intangible assets.

